-
The Everest Ransomware Group claims to have compromised over 1.4 TB of internal and customer data from Iron Mountain.
-
The gang also hit 6 other major corporations, and among those are millions upon millions of personal healthcare records.
-
They have also imposed a deadline for February 11 by which Iron Mountain must pay to avoid having their database publicly exposed.

A major ransomware group is on a spree. It has just added several big-name companies to its hit list.
The fallout could be severe. Stolen data includes sensitive patient medical records and terabytes of corporate secrets.
The Everest Gang’s Newest Victims
Everest, a ransomware group affiliated to Russia appears to be very active lately. The latest posts on their leak site, shows they have recently added seven more victims to their list of organizations whose data they are going to release on the dark web.
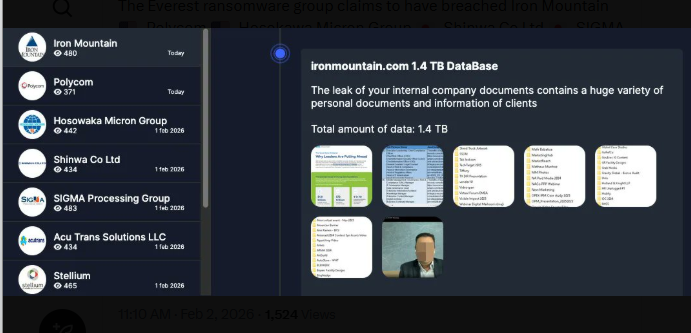
Photo credit: X
The alleged victims include U.S. information management leader Iron Mountain, video conferencing giant Polycom (now part of HP), and Acu Trans Solutions LLC, a medical transcription service. Also named are Japanese firms Hosokawa Micron Group and Shinwa Co Ltd, Panama’s SIGMA Processing Group, and U.S. consultancy Stellium.
The gang claims to have stolen terabytes of data. They say it spans sensitive internal documents and critical client information across all these companies.
Iron Mountain Data and Acu Trans Solutions Risk Exposing 1.4 TB of Data and Medical Records
The claim against Iron Mountain is particularly alarming. The S&P 500 company is a global vault for physical and digital information.
Everest claims it stole 1.4 terabytes from Iron Mountain. The data reportedly includes internal documents and client information. As proof, the hackers posted screenshots of folder names. These names suggest client data was exposed.
Iron Mountain has not confirmed if the claims are true. Withholding the full data is often how attackers hold companies at ransom. It is a warning shot to force payment.
Another high-risk breach involves Acu Trans Solutions LLC. Everest says they stole 253 gigabytes of very sensitive medical information, including Electronic Medical Records (EMRs) and private patient data.
Exposing people’s medical records is a serious violation of medical privacy because it places patients at a risk of identity theft or fraud.
An Increasing Pattern of Global Threats
The other listed victims also face serious exposure. Everest claims to have stolen 360 GB of internal documents and client invoices from supply chain firm Stellium. They also allege 90 GB from Polycom, 42 GB from Shinwa, 30 GB from Hosokawa Micron, and 19 GB of financial records from SIGMA Processing.
This spree shows a pattern of aggressive, multi-national attacks. The gang is targeting diverse sectors. These range from construction and manufacturing to finance and technology.
This reflects a wider ecosystem where cybercriminal groups routinely target major consumer-facing businesses, as seen in the recent claim by a hacker group of a Panera Bread data breach exposing 14 million customer records.
For each victim, Everest has posted a countdown clock on its leak site. The timer on Iron Mountain’s ransom is set to expire on February 11. It’s a common tactic attackers use to pressure companies into negotiating with them to avoid their private data being published or sold online.
The potential impact of this kind of breach is tremendous. If there is any truth in Everest’s claims, a lot of corporate secrets, including financial details and very confidential personal data, are at risk of being out in the open for criminals to prey on.
The situation remains fluid as the listed companies investigate. The cybersecurity community is watching closely. They wait to see if the threatened data leaks will become a damaging reality, as they tragically did for patients in the recent ransomware attack on a Columbia medical practice.