-
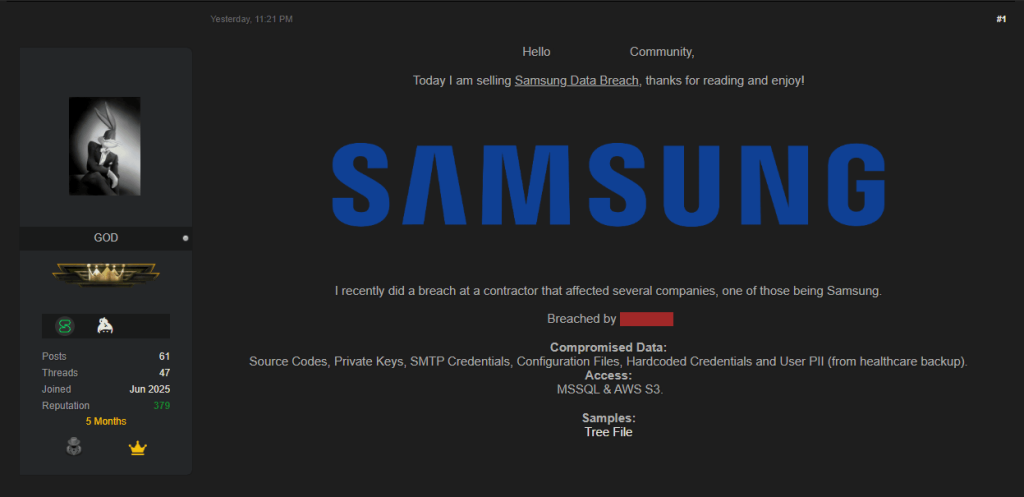
A cybercriminal called 888 is currently advertising purported Samsung internal records on a dark web illicit forum.
-
888 claims to have stolen the details through a vulnerability in one of Samsung’s third-party contractor’s sites.
-
The hacker advertised various data including access to AWS S3 and MSSQL, providing evidence that the hack was done against Samsung’s Medison healthcare systems.
In recent activities involving the cybersecurity sector, Samsung appears to be the latest victim of the cybersecurity threat actor known as 888. According to a recent report, 888 took to the public, announcing on a cybercrime online forum that it had breached into Samsung’s systems.
On the platform, the hacker advertised supposed internal records from the global tech giant, Samsung, possibly exposing sensitive information.
Threat Actor Advertises Samsung Internal Records on Dark Web Forum
In the recent report, 888 claimed to have exfiltrated the data via an attack against the digital systems used by one of Samsung’s third-party contractors. The hacker also provided a vast array of details, such as private keys, customer personally identifiable information (PII), and source codes from a healthcare backup unit.
Furthermore, the exposed database also comprises AWS S3 and MSSQL access details. 888 provided proof that they exfiltrated the datasets from Samsung’s Medison healthcare platform and is currently seeking buyers for the stolen data. 888 asked to receive payments in Monero XMR cryptocurrency, to make sure that no one can trace their digital footprints & make it even more difficult for anyone to trace transactions.
While Samsung, or any of its subsidiaries, has yet to confirm this breach, it is still threatening to security & privacy. Primarily, due to the sensitive nature of data from the healthcare industry, a hack of this kind can be catastrophic for both customers and Samsung’s healthcare branch.
It is worth noting that the healthcare sector has been a primary target for online hackers recently, as it possesses a vast database of customers, workers, clients, and government agencies and officials. This incident follows a clear pattern of healthcare data being auctioned on hidden forums, as seen in the recent case where patient data from a doctor alliance breach hit the dark web.
Personic Data Breach Affects 10,929 Individuals Nationwide
In a similar development, Personic Management Company experienced a significant data breach, which impacted 10,929 customers in the US. The cyberattack took place on September 1, 2025, whereby an anonymous threat actor gained access through one of the firm’s third-party software platforms, which Personic uses for patient management.
Notably, the compromised details may comprise full names, dates of birth, contact details, medical records, driver’s licenses, Social Security Numbers (SSNs), and state ID numbers, among many others.
On November 18, 2025, Personic reported the hack incident to the Maine and New Hampshire offices of the Attorney Generals. The following day, the firm reported the data breach to the Texas Attorney General’s office.
It is worth stating that because of the leak of protected health details, both existing and previous patients of the healthcare firm are at risk of medical fraud or identity theft. Personic has also started reaching out to the affected individuals through mail.
Furthermore, the firm commenced investigations and employed steps to bolster its digital security and data management practices. The firm has also offered to cover 24 months of complimentary identity protection and credit monitoring services via Cyberscout.
Therefore, affected individuals can reach out to Personic by email, call at 833-716-2114.
